The Power of Continuous Security Monitoring
With complete security synchronicity, CSM fosters a proactive and resilient defense strategy in an era where digital threats are ever-present and constantly evolving.
Let’s understand your options. 👇
With complete security synchronicity, CSM fosters a proactive and resilient defense strategy in an era where digital threats are ever-present and constantly evolving.
Let’s understand your options. 👇
It’s no secret that companies are experiencing more breaches than in recent years. According to IBM, the average cost of each breach is just over $4.45 million.
Many cybersecurity professionals beg the question, “If we have more solutions now and cybersecurity spending is higher than it’s ever been, why are we experiencing an unprecedented amount of breaches?”
Great question!
The most commonly overlooked causes of rising data breaches are:
We’re funneling our cybersecurity budgets into fragmented solutions. How you spend your budget is far more critical than how much you spend. We’ve got a solution that optimizes your budget and keeps your enterprise out of the line of fire. 👇
Continuous Security Monitoring is a dynamic cybersecurity approach that involves real-time monitoring and analysis of an organization’s information systems. Unlike traditional security measures that rely on periodic scans and updates, CSM operates around the clock, providing a continuous, vigilant eye on potential threats.
In a rapidly evolving threat landscape, the continuous, real-time nature of CSM provides a robust defense, enabling organizations to stay one step ahead of cyber criminals by providing:
With complete security synchronicity, CSM fosters a proactive and resilient defense strategy in an era where digital threats are ever-present and constantly evolving.
Now, let’s understand your options.
With IT infrastructure evolving quicker, it’s vitally important that security gaps are identified and alleviated before they are exploited. While Pen testing is a great first step at pinpointing these threats, they lack the continuity that’s needed to keep up with the shifts.
True knowledge allows your security teams to avoid being inundated with faulty or inaccurate threats and allows your team to focus their resources on correcting the real security gaps. With CSM, cybersecurity professionals can strategically and precisely remediate with new data based on the threats’ real impact on their business and ultimately, their bottom line.
Let’s take a look at security platforms that do just that and put your security back in your hands.
Pentera offers agentless, real (not simulated), and safe exploitation of vulnerabilities, also known as Automated Security Validation which “continuously monitor an organization’s internal and external attack surfaces. Pentera reveals the adversary’s perspective to highlight the most attractive targets on the entire attack surface.”
Improve your testing capabilities and validate your existing security controls with continuous penetration testing. Ensure your attack surface is safe through actionable intelligence and insights, making it easy to manage security gaps, understand the exploitable vulnerabilities, remediate exploitable vulnerabilities, and prioritize exploitable vulnerabilities based on the impact they have on the network.
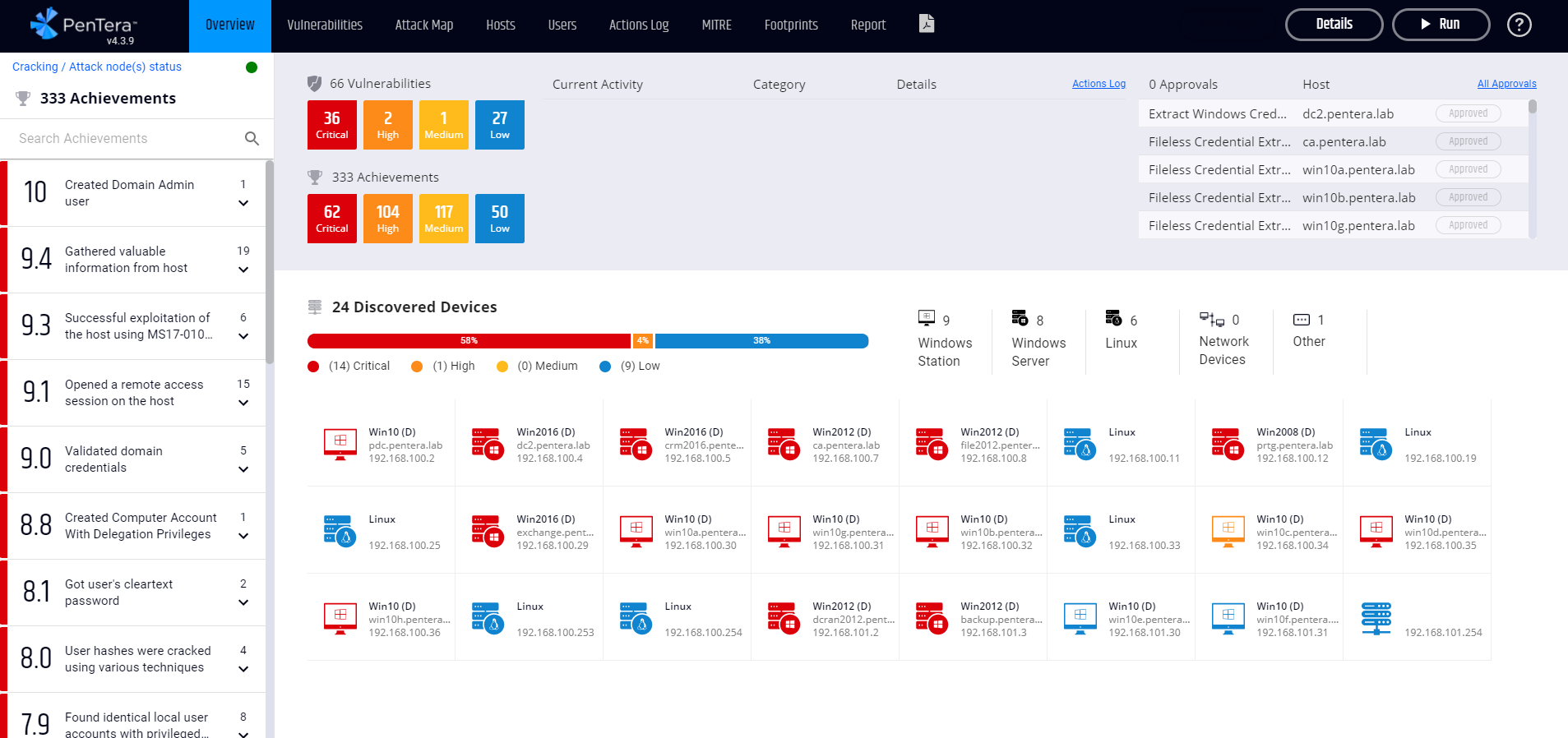
Leverage their solution in a number of ways 👇
Step 1: Know your attack surface
Pentera maps your attack surface including exposed credentials found on the deep, dark, and open web to understand what credentials have been compromised, and the impact that they may have on your external and internal attack surface.
Step 2: Challenge your attack surface
Pentera then safely exploits the data mapped during Step 1 using the latest attack techniques and uncovers security gaps. These include more dynamic type vulnerabilities such as EDR evasion, malware, and ransomware. All built and designed by Pentera’s research/development teams to ensure safety by design.
Step 3: Prioritize remediation by impact
What’s the business impact of each exploitable vulnerability? Pentera identifies the attacks with the greatest impact and prioritizes them based on the root cause of each attack and the impact that it has on your network.
Step 4: Apply remediation recipes
Remediation lists, along with detailed step-by-step instructions (wiki), are supplied to address security gaps. Finally the Pentera solution will highlight how to run a test scenario once the changes to the network have been completed in order to confirm the positive impact on your overall IT security posture.
🚀 Looking for an automated solution for continuous security stack testing? Request a demo today.
The Axonius Platform, “gives customers a comprehensive understanding of all assets, their relationships, and business-level context. By connecting to hundreds of data sources and aggregating, normalizing, deduplicating, and correlating data about devices, identities, cloud, software, SaaS applications, vulnerabilities, security controls, and their interrelationships, customers can ask questions, get answers, and automate action.”
Legacy CMDB relies heavily on agent scanning for asset discovery while being costly to maintain.
Traditional CMDB lacks any capability to integrate into different data sources and complex infrastructures. Extracting and correlating data can be labor intensive and takes your security team away from providing attention to more pertinent aspects of your environment.
Axonius aims to broaden the scope of what companies can see inside their security environment, creating better asset visibility, and automating policy enforcement. If there’s a gap in your security policies, Axonius will spot it. 🔎
What does Axonius do better than a traditional CMDB? 👇
Axonius seamlessly integrates 850+ security and IT management solutions, deploying incident response, vulnerability, and patch management in hours!
🚀 Supercharge your network today– get started with a demo.
CyCognito empowers companies to take full control over their attack surface by uncovering and eliminating critical security risks they didn’t even know existed.
Threat actors search for the path of least resistance, and the Cycognito platform performs attacker-like reconnaissance, discovers all unknown unknown assets, assesses the vulnerabilities, and then guides you on what to fix first to reduce the most risk.
Use Cases:
Continuous Security Monitoring and Attack Surface Management isn’t just a security measure; it’s a mindset shift toward proactive cybersecurity. In an ever-evolving, shifting digital landscape, organizations must adopt equally dynamic strategies. Implementing CSM not only fortifies defenses but also instills confidence in stakeholders, demonstrating a commitment to the ongoing battle against cyber threats. Avoid funneling hundreds of thousands if not millions of dollars into fragmented, disjointed security solutions and focus on streamlining your security solutions.
CSM is the key to unlocking a future of resilience and digital trust.
As we continue to evolve our security systems to meet digital expectations, your team must be prepared for the attacks ahead. Our team has proven solutions to keep your security infrastructure proactive, not reactive, helping you on your journey to creating a resilient network.
If you have any questions regarding securing your network, contact either tom.barnes@avexonsecurity.com or collin.mckinzie@avexonsecurity.com.